jhungary
MILITARY PROFESSIONAL

- Joined
- Oct 24, 2012
- Messages
- 19,294
- Reaction score
- 387
- Country
- Location
Understanding Counter-Intelligence (Counter-HUMINT)
Several months ago (may have been years in fact), I have wrote a detail article on HUMINT and how HUMINT Op are planned and operated. After some member here (Noticeably @TaiShang and gang) say that I am full of shite. So, today I am gonna tell you guys a lot more about Intelligence Activities and this time I will spin the story around and look at intelligence issue on another angle, the counter-intelligence.
Upon reading this article, you would have a basic understanding of the following topic.
What is Counter Intelligence (CI)
Counter Intelligence (Refer to as CI below) is an activities that a country do to prevent other's intelligence activities conducted by foreign entities on their own soil. The concept is quite complex as most of the CI works related to one's own Intelligence activities, hence some country would designate CI into Intelligence/Counterintelligence (I/CI)
Since the beginning of time, when there are 2 countries in hostilities, they would have conduct intelligence activities (or espionage) toward each other. On one hand you want to penetrate into your target network, on the other, you want to prevent your own network being penetrated. Hence CI was born
The goal of CI is to discover, delay (or interrupt) and destroy (3D) your enemy intelligence network. The mean to get to the this stage is mostly depends on one's own intelligence network, as to how to turn enemy's agent or how to uncover any underground network and etc.
CI being an integral part of Intelligence Cycle Security, Along with Operational Activities and Operational Security (OPSEC) formed the Intelligence Cycle Security. And intelligence cycle itself is a part of Greater Chain of Intelligence Cycle Management which is the part of Intelligence Cycle itself, but in this article, I will not talk about all these (Most of them are classified anyway) and will focus on CI itself as an independent topics.
Who is responsible for CI activities?

Again, different country have different rules, and I cannot be an expert of all (Although I have been an expert on some Intelligence network....) So in this article, I will focus on CI activities carried out by the United States.
There are currently 2 Parent organisation in charge of CI activities which both worked jointly but because of the nature of the business, 2 separate entities are needed. They are:
Under DIA (Which is similar to British MI-6) the Military Intelligence cycle are then further divided into each branch of Military and each branch have its own Intelligence and Counter Intelligence unit under its command. The premier CI service in each branch of US military are:
INSCOM - 902 MI Group

The 902nd Military Intelligence Group under the command of United States Army Intelligence and Security Command are the premier counterintelligence group within the US Army, this is the same group I was last deployed to.
902 MIG was an cooperation between NSA and US Army, under the INSCOM (technically it's the INSCOM that were in cooperation between NSA and USA) The Group have 5 components. Which directed at different task within different intelligence level.
HQ Detachment 902 MIG - In charge of Command, Personnel and Logistic Affair
308th Military Intelligence Brigade - In charge of investigation and operation on CI, CT and Counter Espionage within the US (CONUS)
310th Military Intelligence Brigade - In charge of investigation and operation on CI, CT and Counter Espionage outside the US (OCONUS)
752nd Military Intelligence Brigade - In charge of conducting CI activities to support CI, CT and Counter Espionage effort worldwide. In other word, it provide the basic frameworks and service package tailor to every operation behind the scenes, the brain of CI
The Army Operational Security Detachment - Special Force member (or SF qualified MIG Member) group tasked to execute those intelligence operation in support of CI efforts.
Another establishment of the 902MIG is the Army Counterintelligence Center - Which is to provide information, resource and training to any of the USCI Agent.
However, the TO&E (Table of Organisation and Equipment) is that each US Army regular units (Unit Such as 1st infantry division) would have their own CI capability, and the enhancement of such capability would be by CI detachment, hence most CI agent are Airborne and Ranger Trained so that it can provide CI activities support in any given situation.
Of course the daily operation and the mission statement are all classified, so this is not within my place to disclose such works.
Types of counter intelligence activities
Before knowing the type of CI activities, there are needed to discuss the CI Cycle, which formed the base line for all CI activities.
The CI Cycle is
1.) Collective Counterintelligence
2.) Defensive Counterintelligence
3.) Offensive Counterintelligence
Collective Counterintelligence
The word collective means (By-all-means) in a sense that you as a CI agency, try to use information by all means to build your potential enemies capability. By building a picture of an enemy, you knows what they would be basically capable of and then you can predict and prevent the enemy to use their capability to penetrate your own network.
An estimation of enemy capability would build a perfect picture of your enemies capability and your own agency can then use this information to counter any penetration. There are good number of ways this can be done in preventive measure, method can be covert or overt. From using your own HUMINT (asset acquisition) to interrogation of enemy EPW or Intelligence agent.
Defensive Counterintelligence
Defensive Counterintelligence mostly evolved about establish security and thus understanding one own weak point and focus on detecting FIS activities in those weak point.
Basically, there are Defensive Counterintelligence plan for each intelligence discipline. Agents are train with specific discipline in mind.
What you look for a Defensive Counter-HUMINT Ops?
As said before, the basis of CI activities is to detect-identify-counter-neutralize. To start, one must find out where to look for. There are always tell-tale sign one may be of Security Threat, even one may hold the highest security clearance.
The first stage is detect. Basically, when something under your control starting to go wrong, there are almost always a threat being developed. Information stopped coming in, or project you are handling always over before you even begin, then there are good chances what you are experience is some sort of security breach, maybe your position had been intruded by FIS or maybe some trusted person shot their mouth off. You don't know, but that is a good way to look at it closely.
Then once you have detected a threat, the next step is that you need to know where it came from, thus, identifying the threat. It's always not as easy as it seems, but what you look for is something that wasn't right. Things like are any new member in the team? Or is anyone under some kind of duress? (Such as family and financial) and then you need to look closely at which and where the foreign entity can possibly obtain such information to inhabit your own intelligence work.
Now you may have been ID'ed the threat, but you may not know for sure if this is actually the threats. What you would need is to confirmation. Usually by the way of misinformation. The Basic premise is like this, you pipe down a different or false (Otherwise known as controlled) information to your suspected leak, then you wait and see which scenario panned out. Then you will have your leak.
The third step started once you identified your leak, then you are to think of a way to counter it, that would involve a series of assessment, once you assessed the situation, then you will choose the most appropriate way to counter this problem.
Assessment done to the leak would determine the later course of action, should he/she be outright prosecuted? Or should he/she would be deemed important or trust worthy to turn and work for you? Sadly the assessment done in this stage is highly classified, I cannot tell you how assessment were done to individual threat, but in general, if he/she is important enough (Which effective benefit your own agency if they were turned) or if the asset is a trusted source to your enemy (You cannot turn an agent if they were not trusted by their own handler) This will affect the course of action to be taken later.
Which lead us to the final step, the decision to neutralize or to exploit them. To neutralize may not always means to kill (even tho this is one express action one can take) Neutralize means neutralize the threat present, either by taken them down or left them in place as an unwilling and unwitting participant to your counter-intelligence game.
Or if you can exploit them, meaning you use them to your own interest, then you will turn the agent into a double agent. Again, only if it was deemed possible in the assessment.
Offensive Counterintelligence
Offensive counterintelligence is basically you take the fight over to your enemy, by disrupting and impeding your enemy's intelligence gathering capability, thus you don't wait for your enemy to make their first move (by active penetrating your own network) you make your first move to them.
Offensive Counterintelligence can only be done with Human Interaction. Not to be confused with you can only do offensive counterintelligence on HUMINT, you can still start offensive campaign on other enemy spectrum (such as ELINT) but this will nonetheless involve human interaction. Hence a human agent would be involved. Most to all Offensive Counterintelligence are also called Counter-Espionage Activities.
The way it works is to make your enemy paid to capture your own intelligence. Every kind of penetration require resource to pull off (Such as time to train an agent and money to put in any operation) The goal of offensive counter intelligence is to make your enemy chasing tail and start believing in non-existent threat and thus they have to replace or send in new agent, in the process, money and resource will be spend, and chances they will got caught.
Think of it this way, if you own agent conduct offensive campaign within the enemies own intelligence agency and sabotage the progress of those ops, your enemy will started to think their ops did not round up any result. And they will either have to replace those who are in place (which could have been nothing wrong to begin with) and send in new agent or multiple agent to get result, in the process, chances are they could be caught, turned or at least link to your enemies, thus reviewing your enemy's capability.
Offensive Counterintelligence take advantage of the compartmental characteristic of intelligence service which no one fraction know what or who is behind another one in order to protect the source integrity, this also means each one of the case officer would not know the detail of the other agent operate by another case officer. And information came in compartmentalized. Which make it vulnerable to be attack from within.
However, carrying out an offensive counterintelligence ops is not easy. One have to look beyond the scope of "Detect-Identify-Counter-Neutralize". The role of offensive counterintelligence would have include several factors as well, such as trust issue and manipulation
At one point or another, be it a mole or a turned double agent, your won agent have to manipulate someone or something along the road to get to what it wants. You either have to manipulate your enemy agent or your enemy organisation to get to conduct an offensive counterintelligence ops.
Case Study - Double Cross system in WW2.
The Double Cross system is a operation conducted by MI5 during WW2 and was a prime example of Defensive and Offensive Counterintelligence due to its high success.
Post war document shown the British Successfully used the Double Cross system to detect and turn or deal with all German Agent sent to the UK during the whole WW2 expect for one German Agent that committed suicide before MI5 can reach out to it.
Where Double Cross system (XX) started off as an counter intelligence operation aimed to look for German Agent working within the UK during the height of WW2, the Spy-Mania which Churchill dubbed have heighten the myth that many well train
German Agent walks the street of Britain and they were well implanted into their own society, the program starts as a Defensive Counterintelligence Operation aimed to flush out those agent.
However, facts cannot be further away from the truth, as it turns out, the G0erman agents were mostly untrained Eastern European background who were captured due to its inability or unable to blend in with the general British Society. Those agents (25 in total were quickly arrested.
What follow is that while some of these German Agent will be imprisoned or executed, some were retained as double agent. And the myth have also allow Germany to believe their operation in the UK were a big success. (Nobody actually know if Churchill overblown the whole situation or in on the XX operation in the beginning) Thus sending more agent into turned Eastern European German Agent and their handler.
That means from that moment on, the XX system had turn from being an Defensive Counterintelligence Operation to an Offensive one. As German Agent start arriving on the British Coast, one by one they were capture, turned and put back into position, tricking the German into believe they program is a success and in the process, hijack the German Spies Network into working for MI5 favor.
As a result, all of the German Agent send during WW2 by Germany were captured and turned before Germany can put them to work.
The working principal behind counter intelligence
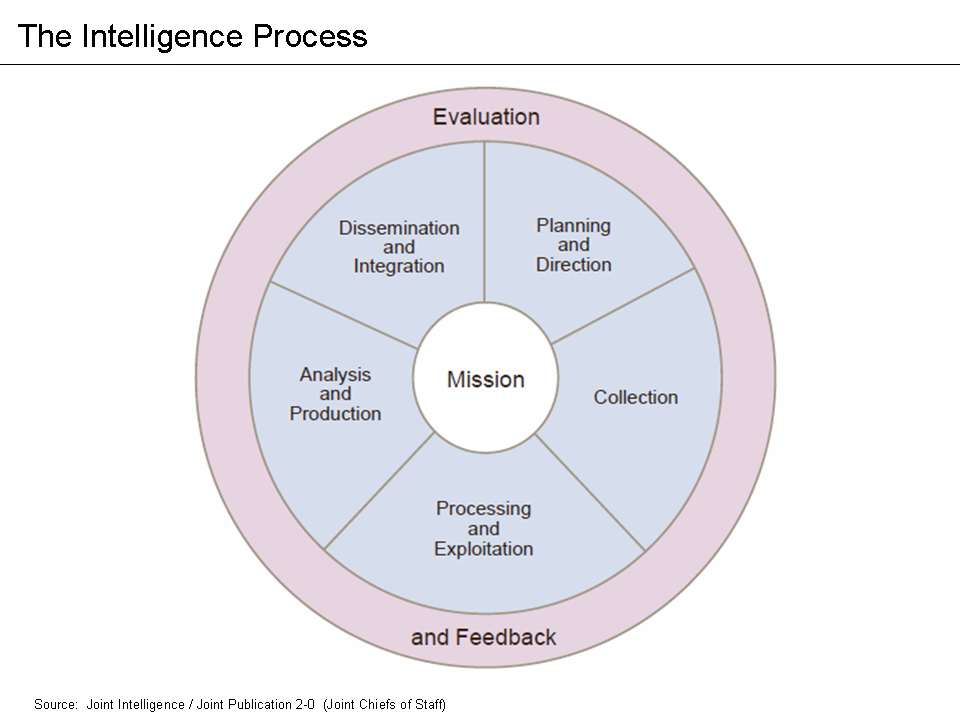
As part of Intelligence Security Cycle. CI works hand-in-hand with operational security and operational activities. The Cycle also predict where CI is going to be needed.
In a perfect world, if OPSEC cannot be broken, there will be no need for any CI works to be done, but in reality, OPSEC are always broken, either by choice or by accident. And it would be important (or at least equally important) for Counterintelligence to Protect the intelligence integrity and for the operational activities to enforce this integrity.
Where the mission itself could have seen as a part of overall intelligent activities or espionage. The way to counter enemies intelligence activities have always be favoured in the intelligence community, to begin with, CI usually conduct within your own soil (With the exception of offensive counterintelligence) which minimize the risk to your own personnel in a hostile environment.
Also, by committing into CI, there could also be a positive effect as to improve other entities within the cycle. OPSEC can be improved with every enemy spy caught and it also leads to the operation become smoother on your own side.
Thus the cycle can work to benefit each other, where the OPSEC will protect the Operational Activities and the CI will protect the OPSEC by plugging the leak, and Operational Activities would then be able to benefit CI by expanding the network. And that is the working principle behind Counter Intelligence
And that's for today article, I hope you enjoy reading it, as usual, any question that did not cross over the boundary of national security will be answer. Thanks for your time, hope to see you next time.
Several months ago (may have been years in fact), I have wrote a detail article on HUMINT and how HUMINT Op are planned and operated. After some member here (Noticeably @TaiShang and gang) say that I am full of shite. So, today I am gonna tell you guys a lot more about Intelligence Activities and this time I will spin the story around and look at intelligence issue on another angle, the counter-intelligence.
Upon reading this article, you would have a basic understanding of the following topic.
- The definition of counter intelligence
- Organisational Structure of Counter Intelligence Agency
- Types of counter intelligence activities
- The working principal behind counter intelligence
What is Counter Intelligence (CI)
Counter Intelligence (Refer to as CI below) is an activities that a country do to prevent other's intelligence activities conducted by foreign entities on their own soil. The concept is quite complex as most of the CI works related to one's own Intelligence activities, hence some country would designate CI into Intelligence/Counterintelligence (I/CI)
Since the beginning of time, when there are 2 countries in hostilities, they would have conduct intelligence activities (or espionage) toward each other. On one hand you want to penetrate into your target network, on the other, you want to prevent your own network being penetrated. Hence CI was born
The goal of CI is to discover, delay (or interrupt) and destroy (3D) your enemy intelligence network. The mean to get to the this stage is mostly depends on one's own intelligence network, as to how to turn enemy's agent or how to uncover any underground network and etc.
CI being an integral part of Intelligence Cycle Security, Along with Operational Activities and Operational Security (OPSEC) formed the Intelligence Cycle Security. And intelligence cycle itself is a part of Greater Chain of Intelligence Cycle Management which is the part of Intelligence Cycle itself, but in this article, I will not talk about all these (Most of them are classified anyway) and will focus on CI itself as an independent topics.
Who is responsible for CI activities?
Again, different country have different rules, and I cannot be an expert of all (Although I have been an expert on some Intelligence network....) So in this article, I will focus on CI activities carried out by the United States.
There are currently 2 Parent organisation in charge of CI activities which both worked jointly but because of the nature of the business, 2 separate entities are needed. They are:
- Defence Intelligence Agency (DIA) which operate Defence Clandestine Services
- Central Intelligence Agency (CIA) which operate Directorate of Operation (Formerly known as National Clandestine Services)
Under DIA (Which is similar to British MI-6) the Military Intelligence cycle are then further divided into each branch of Military and each branch have its own Intelligence and Counter Intelligence unit under its command. The premier CI service in each branch of US military are:
- US Army - United States Army Counterintelligence INSCOM-902 MI Group (USCI)
- US Navy - Navy Criminal Investigative Service (NCIS)
- US Navy - Office of Naval Intelligence (ONI)
- US AF - Air Force Office of Special Investigation (AFOSI)
- US Marine - Marine Corps Intelligence Activities (MCIA)
- US Coast Guard - Coast Guard Counterintelligence Service (CGCS)
INSCOM - 902 MI Group
The 902nd Military Intelligence Group under the command of United States Army Intelligence and Security Command are the premier counterintelligence group within the US Army, this is the same group I was last deployed to.
902 MIG was an cooperation between NSA and US Army, under the INSCOM (technically it's the INSCOM that were in cooperation between NSA and USA) The Group have 5 components. Which directed at different task within different intelligence level.
HQ Detachment 902 MIG - In charge of Command, Personnel and Logistic Affair
308th Military Intelligence Brigade - In charge of investigation and operation on CI, CT and Counter Espionage within the US (CONUS)
310th Military Intelligence Brigade - In charge of investigation and operation on CI, CT and Counter Espionage outside the US (OCONUS)
752nd Military Intelligence Brigade - In charge of conducting CI activities to support CI, CT and Counter Espionage effort worldwide. In other word, it provide the basic frameworks and service package tailor to every operation behind the scenes, the brain of CI
The Army Operational Security Detachment - Special Force member (or SF qualified MIG Member) group tasked to execute those intelligence operation in support of CI efforts.
Another establishment of the 902MIG is the Army Counterintelligence Center - Which is to provide information, resource and training to any of the USCI Agent.
However, the TO&E (Table of Organisation and Equipment) is that each US Army regular units (Unit Such as 1st infantry division) would have their own CI capability, and the enhancement of such capability would be by CI detachment, hence most CI agent are Airborne and Ranger Trained so that it can provide CI activities support in any given situation.
Of course the daily operation and the mission statement are all classified, so this is not within my place to disclose such works.
Types of counter intelligence activities
Before knowing the type of CI activities, there are needed to discuss the CI Cycle, which formed the base line for all CI activities.
The CI Cycle is
- Detect
- Identify
- Assess and Counter
- Neutralize or Exploit.
1.) Collective Counterintelligence
2.) Defensive Counterintelligence
3.) Offensive Counterintelligence
Collective Counterintelligence
The word collective means (By-all-means) in a sense that you as a CI agency, try to use information by all means to build your potential enemies capability. By building a picture of an enemy, you knows what they would be basically capable of and then you can predict and prevent the enemy to use their capability to penetrate your own network.
An estimation of enemy capability would build a perfect picture of your enemies capability and your own agency can then use this information to counter any penetration. There are good number of ways this can be done in preventive measure, method can be covert or overt. From using your own HUMINT (asset acquisition) to interrogation of enemy EPW or Intelligence agent.
Defensive Counterintelligence
Defensive Counterintelligence mostly evolved about establish security and thus understanding one own weak point and focus on detecting FIS activities in those weak point.
Basically, there are Defensive Counterintelligence plan for each intelligence discipline. Agents are train with specific discipline in mind.
- Counter-HUMINT
- Counter-SIGINT
- Counter-IMINT
- Counter-OSINT
- Counter-MASINT
What you look for a Defensive Counter-HUMINT Ops?
As said before, the basis of CI activities is to detect-identify-counter-neutralize. To start, one must find out where to look for. There are always tell-tale sign one may be of Security Threat, even one may hold the highest security clearance.
The first stage is detect. Basically, when something under your control starting to go wrong, there are almost always a threat being developed. Information stopped coming in, or project you are handling always over before you even begin, then there are good chances what you are experience is some sort of security breach, maybe your position had been intruded by FIS or maybe some trusted person shot their mouth off. You don't know, but that is a good way to look at it closely.
Then once you have detected a threat, the next step is that you need to know where it came from, thus, identifying the threat. It's always not as easy as it seems, but what you look for is something that wasn't right. Things like are any new member in the team? Or is anyone under some kind of duress? (Such as family and financial) and then you need to look closely at which and where the foreign entity can possibly obtain such information to inhabit your own intelligence work.
Now you may have been ID'ed the threat, but you may not know for sure if this is actually the threats. What you would need is to confirmation. Usually by the way of misinformation. The Basic premise is like this, you pipe down a different or false (Otherwise known as controlled) information to your suspected leak, then you wait and see which scenario panned out. Then you will have your leak.
The third step started once you identified your leak, then you are to think of a way to counter it, that would involve a series of assessment, once you assessed the situation, then you will choose the most appropriate way to counter this problem.
Assessment done to the leak would determine the later course of action, should he/she be outright prosecuted? Or should he/she would be deemed important or trust worthy to turn and work for you? Sadly the assessment done in this stage is highly classified, I cannot tell you how assessment were done to individual threat, but in general, if he/she is important enough (Which effective benefit your own agency if they were turned) or if the asset is a trusted source to your enemy (You cannot turn an agent if they were not trusted by their own handler) This will affect the course of action to be taken later.
Which lead us to the final step, the decision to neutralize or to exploit them. To neutralize may not always means to kill (even tho this is one express action one can take) Neutralize means neutralize the threat present, either by taken them down or left them in place as an unwilling and unwitting participant to your counter-intelligence game.
Or if you can exploit them, meaning you use them to your own interest, then you will turn the agent into a double agent. Again, only if it was deemed possible in the assessment.
Offensive Counterintelligence
Offensive counterintelligence is basically you take the fight over to your enemy, by disrupting and impeding your enemy's intelligence gathering capability, thus you don't wait for your enemy to make their first move (by active penetrating your own network) you make your first move to them.
Offensive Counterintelligence can only be done with Human Interaction. Not to be confused with you can only do offensive counterintelligence on HUMINT, you can still start offensive campaign on other enemy spectrum (such as ELINT) but this will nonetheless involve human interaction. Hence a human agent would be involved. Most to all Offensive Counterintelligence are also called Counter-Espionage Activities.
The way it works is to make your enemy paid to capture your own intelligence. Every kind of penetration require resource to pull off (Such as time to train an agent and money to put in any operation) The goal of offensive counter intelligence is to make your enemy chasing tail and start believing in non-existent threat and thus they have to replace or send in new agent, in the process, money and resource will be spend, and chances they will got caught.
Think of it this way, if you own agent conduct offensive campaign within the enemies own intelligence agency and sabotage the progress of those ops, your enemy will started to think their ops did not round up any result. And they will either have to replace those who are in place (which could have been nothing wrong to begin with) and send in new agent or multiple agent to get result, in the process, chances are they could be caught, turned or at least link to your enemies, thus reviewing your enemy's capability.
Offensive Counterintelligence take advantage of the compartmental characteristic of intelligence service which no one fraction know what or who is behind another one in order to protect the source integrity, this also means each one of the case officer would not know the detail of the other agent operate by another case officer. And information came in compartmentalized. Which make it vulnerable to be attack from within.
However, carrying out an offensive counterintelligence ops is not easy. One have to look beyond the scope of "Detect-Identify-Counter-Neutralize". The role of offensive counterintelligence would have include several factors as well, such as trust issue and manipulation
At one point or another, be it a mole or a turned double agent, your won agent have to manipulate someone or something along the road to get to what it wants. You either have to manipulate your enemy agent or your enemy organisation to get to conduct an offensive counterintelligence ops.
Case Study - Double Cross system in WW2.
The Double Cross system is a operation conducted by MI5 during WW2 and was a prime example of Defensive and Offensive Counterintelligence due to its high success.
Post war document shown the British Successfully used the Double Cross system to detect and turn or deal with all German Agent sent to the UK during the whole WW2 expect for one German Agent that committed suicide before MI5 can reach out to it.
Where Double Cross system (XX) started off as an counter intelligence operation aimed to look for German Agent working within the UK during the height of WW2, the Spy-Mania which Churchill dubbed have heighten the myth that many well train
German Agent walks the street of Britain and they were well implanted into their own society, the program starts as a Defensive Counterintelligence Operation aimed to flush out those agent.
However, facts cannot be further away from the truth, as it turns out, the G0erman agents were mostly untrained Eastern European background who were captured due to its inability or unable to blend in with the general British Society. Those agents (25 in total were quickly arrested.
What follow is that while some of these German Agent will be imprisoned or executed, some were retained as double agent. And the myth have also allow Germany to believe their operation in the UK were a big success. (Nobody actually know if Churchill overblown the whole situation or in on the XX operation in the beginning) Thus sending more agent into turned Eastern European German Agent and their handler.
That means from that moment on, the XX system had turn from being an Defensive Counterintelligence Operation to an Offensive one. As German Agent start arriving on the British Coast, one by one they were capture, turned and put back into position, tricking the German into believe they program is a success and in the process, hijack the German Spies Network into working for MI5 favor.
As a result, all of the German Agent send during WW2 by Germany were captured and turned before Germany can put them to work.
The working principal behind counter intelligence
As part of Intelligence Security Cycle. CI works hand-in-hand with operational security and operational activities. The Cycle also predict where CI is going to be needed.
In a perfect world, if OPSEC cannot be broken, there will be no need for any CI works to be done, but in reality, OPSEC are always broken, either by choice or by accident. And it would be important (or at least equally important) for Counterintelligence to Protect the intelligence integrity and for the operational activities to enforce this integrity.
Where the mission itself could have seen as a part of overall intelligent activities or espionage. The way to counter enemies intelligence activities have always be favoured in the intelligence community, to begin with, CI usually conduct within your own soil (With the exception of offensive counterintelligence) which minimize the risk to your own personnel in a hostile environment.
Also, by committing into CI, there could also be a positive effect as to improve other entities within the cycle. OPSEC can be improved with every enemy spy caught and it also leads to the operation become smoother on your own side.
Thus the cycle can work to benefit each other, where the OPSEC will protect the Operational Activities and the CI will protect the OPSEC by plugging the leak, and Operational Activities would then be able to benefit CI by expanding the network. And that is the working principle behind Counter Intelligence
And that's for today article, I hope you enjoy reading it, as usual, any question that did not cross over the boundary of national security will be answer. Thanks for your time, hope to see you next time.


